UPDATE: Secure Software Development Attestation: A(nother) Government Requirement
By: Melissa Duffy , Andrew Martinez

UPDATE:
As follow-on guidance to Office of Management and Budget’s (OMB) September 14, 2022 memo and the associated Executive Order on Improving the Nation’s Cybersecurity from May 2021, the Cybersecurity and Infrastructure Security Agency of the Department of Homeland Security (CISA) has recently released a draft form for companies to attest to secure software development practices. A copy of the draft form can be found on the agency’s website here.
While OMB’s memo provides direction to agencies, any company that produces software and expects to license to government end users should expect contract clauses requiring a self-attestation.
In addition to the release of a draft common form for self-attestation, an extension to the deadline for compliance is anticipated but not yet confirmed. As noted below, the draft form of common attestation is open to comment until June 26, 2023.
Notable aspects of the draft form include:
The form of self-attestation is open to public comment, which will be accepted until June 26, 2023. They may be submitted electronically using the comment feature here. Additional instructions regarding comments can be found here.
----
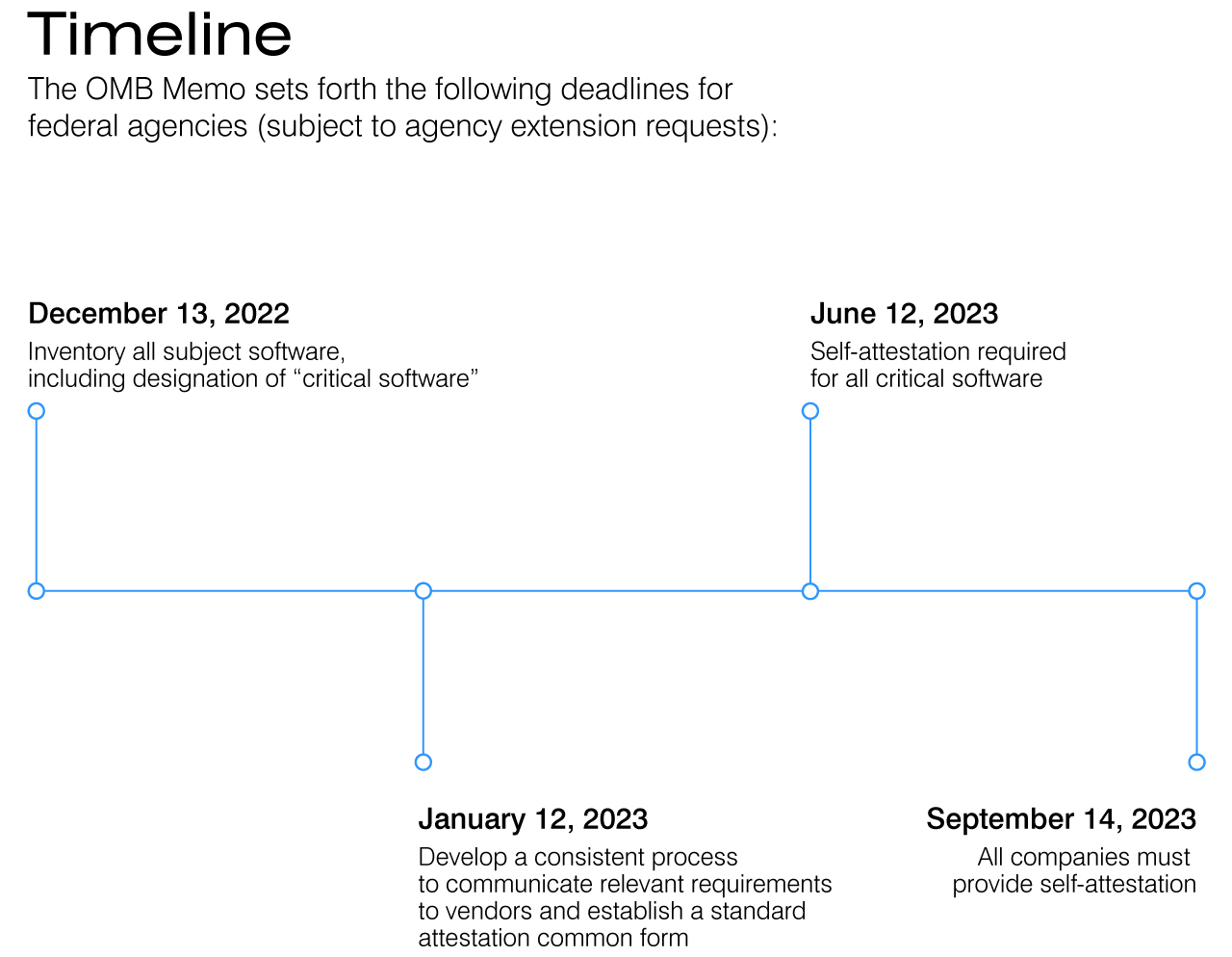
On September 14, 2022, the Office of Management and Budget (“OMB”) issued a memorandum on Enhancing the Security of the Software Supply Chain through Secure Software Development Practices (“OMB Memo”) to help ensure software security. While the OMB Memo provides direction to agencies, any company that produces software (defined as firmware, operating systems, applications and application services, such as cloud-based Software as a Service, or products that include software) and expects to license to government end users must:
These requirements apply to agency (and contractor) use of software developed, as well as the use of existing software that is modified by major version changes, after September 14, 2022.
Background
Last year, President Biden required federal agencies to enhance agency cybersecurity capabilities and protect the nation’s critical software supply chain. See Executive Order 14028 (“Cyber EO”). The Cyber EO tasked NIST with developing guidance on supply chain security which NIST completed in February 2022. NIST developed and published the NIST Guidance consisting of: (1) the Secure Software Development Framework (“SSDF”) Version 1.1 detailing secure software development best practices, and (2) Supply Chain Security Guidance for federal agencies on how to procure software, including open-source software and agency-developed software.
Last week’s OMB Memo requires federal agencies to comply with the NIST Guidance when using third-party “software” on the agency’s information systems or otherwise affecting the agency’s information.
What Must Companies Do:
If a company develops and licenses “software” defined as firmware, operating systems, applications, and application services (such as cloud-based Software as a Service) or products that include software to government entities then the company must determine if their software development process meets the NIST Guidance for secure software development.
Provide a Self-Attestation
After analyzing the software development process against the NIST Guidance, the company must self-attest that it follows those secure development practices – this self-attestation is the “conformance statement” under the NIST Guidance. If a company cannot provide the attestation in the government’s requested format, it can document how it will mitigate those risks in a Plan of Action & Milestones (“POA&M”). In lieu of self-attestation, companies may also provide assessments prepared by certified FedRAMP Third Party Assessor Organizations (“3PAO”). Agencies may require a formal 3PAO assessment depending on the criticality of the product.
The Federal Acquisition Regulatory Council will develop a uniform standard attestation form but until the final rule comes out, any self-attestation must include:
Document your Software Development
The OMB Memo explains that companies may submit to federal agencies artifacts that demonstrate conformance to secure software development practices. Further, the federal agency may require a Software Bill of Materials (“SBOM”) in solicitation requirements, based on the criticality of the software. According to OMB, artifacts other than the SBOM (e.g., from the use of automated tools and processes which validate the integrity of the source code and check for known or potential vulnerabilities) may also be required. Companies should be prepared to provide these documents with solicitation responses and ensure that the sales team is equipped to answer questions regarding secure software development process.
Key Takeaways
Companies providing software or code to the government should: